Cybersecurity in Manufacturing

With the increasing push toward smart manufacturing, cybersecurity has taken center stage in the operational risk profile of manufacturers. A study by Deloitte shows that 48% of manufacturers consider such operational risk as an impediment to smart factory initiatives. As such, cybersecurity in the manufacturing market is poised for growth and is expected to hit $29.85 billion by 2027.
In a recent Manufacturing survey by Omdia, sponsored by Databricks, one of the questions asked was "what are the challenges slowing and even stopping the implementation of analytics and AI Initiatives?". Cybersecurity threats appeared as one of the top two answers, with both answers scoring 44% (see chart below). In fact, in various surveys, cybersecurity consistently rates as a significant challenge across industries.
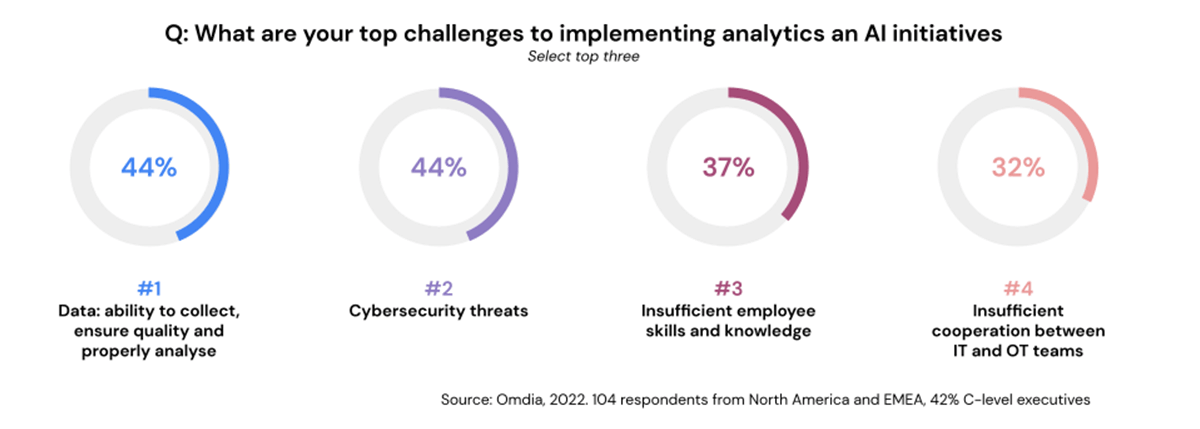
The revenue-risk nature of manufacturing explains why cyber security is such an important topic in the industry; any disruption to production lines through a potential attack can cost thousands of dollars per minute. Such disruptions are the very antithesis of the number one goal of increasing profitability for the industry.
Rethinking cybersecurity for the manufacturing industry
The manufacturing industry is increasingly adopting smart manufacturing practices with unprecedented levels of automation using data and artificial intelligence (AI). In legacy manufacturing operations, air-gapped equipment provided a modicum of protection against cyber attacks. That is not an option anymore, given smart manufacturing often requires greater network connectivity and industrial, internet of things (IIoT) sensing capabilities than legacy practices allow. The silver lining is that the increase in network connectivity opens up the opportunity to bring modern cloud-based technologies such as the Databricks Lakehouse platform to bear on the cybersecurity problems in OT and IoT.
This blurring of boundaries between information technology (IT) systems and operational technology (OT) systems has also greatly increased the attack surface area. In the Colonial Pipeline breach in 2021, the OT system was taken offline as a precaution even though the ransomware had only affected IT systems. The effects of a breach are also no longer isolated to single companies in the modern world of interconnected companies. In 2015, Target's IT system was breached via its HVAC subcontractor company, an entirely separate entity.
The risks and consequences of a breach
The consequences of a breach for manufacturing companies are:
- disruption of operations
- loss of intellectual property (IP)
- loss of life, in the most severe cases.
Ultimately these consequences result in revenue losses and often reputational challenges. Historically, most cybersecurity attacks in the manufacturing industry have focused on disrupting the operations of the plant by targeting the industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. Given that many of these systems may not have internet connectivity, attackers have been creative in their use of alternative vectors of infection, like USB drives. In the case of the Colonial Pipeline breach, their pipeline had to be shut down for six days.
Beyond disrupting operations, attackers also try to steal data, as much of the intellectual property manufacturers own is data around:
- products being manufactured
- the process of manufacturing the product
- the treatments applied to the products when it is utilized
In today's world of smart manufacturing systems, there is an enormous amount of telemetry and log data that can be used to infer the intellectual property in the product, process, or treatments. The Shamoon Hack of 2012 is a prime example of malware that was engineered to steal and wipe out data at the oil company Saudi Aramco. The scale and cost of recovery from this attack were massive - 35,000 computers were partially wiped out or totally destroyed.
Why is cybersecurity so hard?
Investments by manufacturers into cybersecurity for operational technology have traditionally lagged behind that of information technology. This no longer makes sense given the convergence of IT and OT - in essence, manufacturers really need to think of cybersecurity holistically.
On the technology front, OT cybersecurity differs from IT cybersecurity in that installing endpoint detection and response (EDR) agents in ICS or SCADA equipment is often not possible or feasible. Because of that, the security of ICS and SCADA systems typically rely solely on the monitoring of the network traffic to and from these systems. Capturing, storing, and monitoring the voluminous network data is a challenge both from a technology and a cost point of view.
Another challenge in OT security is the capital-intensive nature of manufacturing where the manufacturing equipment is expected to last for decades, often with limited software and firmware updates. The long technology life cycle coupled with limited updates increases the risk of unpatched vulnerabilities in equipment software or firmware. Unpatched vulnerabilities are typically how threat actors get a foothold into the environment. Consequently, OT security measures often need to mitigate the risk from legacy equipment and infrastructure with additional logging and monitoring, which places an additional burden on the data infrastructure.
The lack of investment and the nature of industrial equipment, coupled with an inherently big data problem have created the dearth of manufacturing-oriented cybersecurity tools we face today.
The Databricks Lakehouse for Cybersecurity
In order to build an effective cybersecurity practice teams need to ingest, store and analyze vast amounts of log and telemetry data. This foundational capability is an essential part of IT security standards from ISO/IEC (eg. 27001, 27002) and NIST as well as OT security standards from NERC (eg. 1300) and ISA/IEC (eg. 62443), to name a few. The Databricks Lakehouse Platform is a secure and cost-effective data and AI platform that can ingest, retain, and analyze the log and telemetry data from all your IT and OT systems.
The Lakehouse supports core cybersecurity operations like continuous detection, threat hunting, alert triage, and investigation as well as other applications for risk and compliance with AI and ML. For OT, the logs and telemetry data need to be secured as well, because they may reveal the IP in the proprietary manufacturing processes. Databricks provides terraform blueprints to provision and configure your Databricks Lakehouse using the best practices for securing the workspace.
We recommend the following reference data architecture: Databricks workspace for IIoT data + Databricks workspace for IT/OT/IIoT security data (includes logs from Databricks workspace for IIoT data). Note that this architecture illustrates how log and telemetry data flows from IT systems and OT/IoT systems into a highly-secured Databricks Lakehouse platform in the cloud. This is orthogonal to the Purdue enterprise reference architecture that provides a layered framework for conceptualizing IT and OT systems with respect to segmentation of management and control.
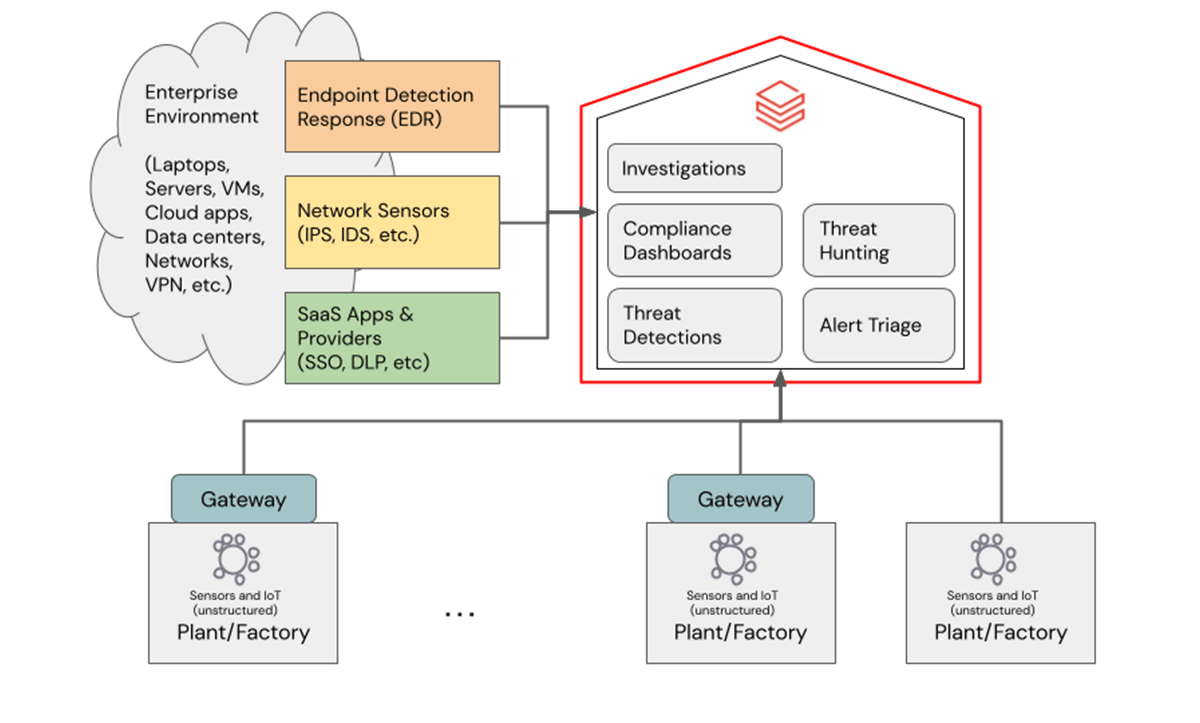
Data within the Databricks Lakehouse Platform is governed by Unity Catalog. Unity Catalog is a unified data governance solution on Databricks that provides fine-grain access controls, metadata search, and discovery, as well as data provenance and lineages. Many manufacturers today, like Rivian, are building big data ecosystems that cut across internally generated data, as well as external data from their suppliers and customers. Unity Catalog also enables data governance and data sharing across organizational boundaries in a secure manner via the open-source Delta Sharing protocol. From a security operations point of view, this is especially relevant when investigating security incidents in collaboration with external security experts and agencies.
Try Databricks Today
We have built Solution Accelerators to help you experience the power of the Databricks Lakehouse Platform and quickly get up and running with your cybersecurity initiatives. Try our Solution Accelerators for DNS analytics and IOC matching today.
Never miss a Databricks post
What's next?

Manufacturing
October 1, 2024/5 min read
From Generalists to Specialists: The Evolution of AI Systems toward Compound AI
Product
November 27, 2024/6 min read
