Is your AI software vendor taking security shortcuts?

This is the final part of our blog series on security available here. In this blog, I will be talking about our culture of security at Databricks.
Artificial intelligence software that can learn and improve human decision-making is transforming business. All sorts of companies are looking to AI to gain an edge over competitors. Unfortunately, everyone is racing to piece together an AI framework, sometimes forging alliances with software vendors that don’t prioritize security—clearly a risky proposition.
Is security a priority for your vendors?
The sprint to build the most competitive AI platform invariably involves partnering with organizations that integrate or make software. So, even if you’re managing your own security effectively, minimizing risk demands similar levels of vigilance from your software partners. It’s a delicate balance—like a dance where each partner has to match or anticipate the other’s next move.
In the pre-cloud days, vendors would build software and hand it over to their customers, leaving them responsible to manage it, regardless of whether they had the necessary expertise in that particular area. In today’s SaaS era, the vendor manages the software, which requires a strong partnership and deep trust between customer and SaaS provider. For the partnership to succeed in the long term, both parties must be linked by trust and transparency, and having a third party audit your vendor’s processes and confirm that their security practices meet or exceed industry standards is key to building both.
Databricks – Security is at our core
Databricks is committed to security first. From day one, we built Databricks as an enterprise software company with a security-first mindset. We’ve created a culture of security best practices, and we work closely with third-party organizations to provide outside-in testing and validation.
We back up our commitment with our technology, earning our customers’ trust by ensuring that our development teams apply industry-leading security practices. We have multiple certifications and rigorous third-party testing and validation, along with regular audits ensuring constant transparency.
Technology built with a security-first mindset
We’ve built many facets of security natively into our data platform, including encryption, identity management, role-based access control, data governance, and compliance standards.
We also take your existing security tools investments into account, with the goal of meeting you where you are. This gives you a range of integrations and controls for your existing security tools, including support for your current identity access management solution using SAML 2.0 and SCIM to simplify setting up and managing accounts on the Databricks platform.
Our security-first mindset extends beyond data access to the architecture itself, with hard segregation between Databricks data and controls planes, leaving the data where it is so we can’t access it. Customers can choose between single or multi-tenant control planes depending on the level of sophistication needed.
Security-minded teams, you can trust
Earning our customers’ trust is our top priority, and we’re committed to fostering security-minded development teams. Through rigorous developer training and ongoing education—and application of security best practices—our development team keeps Databricks solutions bulletproof when it comes to security.
As part of our commitment to maintaining our customers’ trust and helping them mitigate risk, we also:
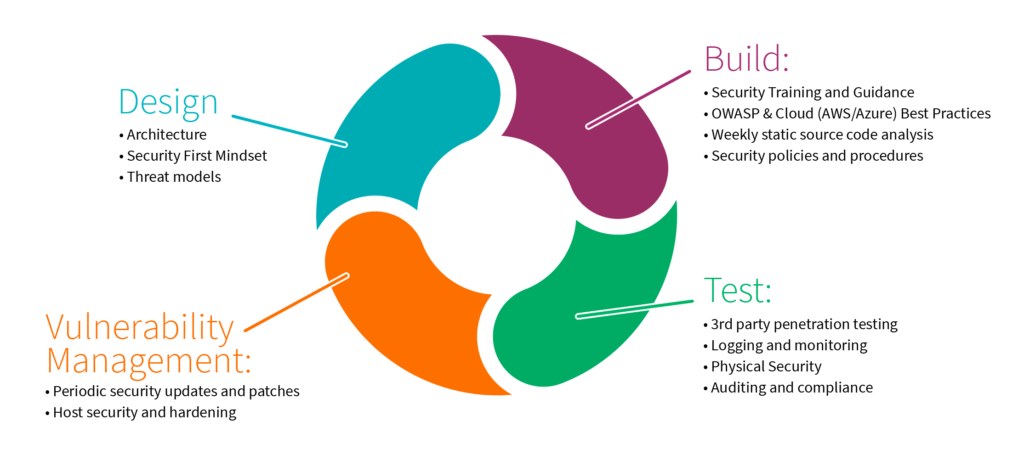
- Ensure that security processes and checks are an integral part of development, by following the Secure System Development Life Cycle (SDLC)
- Make sure all of our developers are well-versed in the security principals essential to their roles with quarterly security training
- Focus on threat modeling, which means running risk assessments throughout the development process and implementing preventative security controls as needed
- Take an “always-be-testing” approach that allows us to identify vulnerabilities early on
- Ensure that the platform is free from security defects, by performing comprehensive quality assurance and penetration testing
Finally, our low engineering attrition rates contribute to continuity and adherence to security best practices.
Transparency through third-party validation
In addition to maintaining the highest level of data security through industry-leading best practices, we also work with independent, PCAOB-registered firms to audit our program regularly and attest to our certifications. We take transparency seriously and make sure our customers understand clearly the intricacies of our platform by making available detailed architectural documentation.
We meet the unique compliance needs of highly regulated industries. We are in compliance with standards such as ISO 27001, SOC 2 Type 2, PCI DSS and HIPAA, along with validation by third-party penetration testing. Our certifications allow us to serve customers in regulated industries, including the Financial Industry Regulatory Authority (FINRA), Sanford Health, and Shell—along with highly sensitive government agencies.
We’re unique in our ability to support customers with GDPR compliance, particularly those using data lakes to store sensitive data that might be subject to a data subject request (DSR). Databricks is also architected so you’re always in control of where your data resides.
We are in the process of completing our Privacy Shield certification and have certified services under SOC 2 Type II and ISO 27001. We also recently attested to ISO 27018, the internationally recognized industry-standard approach for protecting personal data in the cloud.
Partner with us
Security is an increasingly critical part of AI initiatives, which means you need to partner with an organization that doesn’t take security shortcuts. Databricks is committed to being your partner over the long haul, with security deeply embedded in our culture.
Try It!
- Call us to find out how Databricks can improve your security posture.
- Learn more by downloading our security e-book Protecting Enterprise Data on Apache Spark.
Never miss a Databricks post
What's next?

Product
November 21, 2024/3 min read
How to present and share your Notebook insights in AI/BI Dashboards

Product
December 10, 2024/7 min read