Security & Trust Center
Your data security is our top priority
Security Best Practices
For the Databricks Data Intelligence Platform
Secure your deployments
Databricks has worked with thousands of customers to securely deploy the Databricks Data Intelligence Platform with the appropriate features to meet their security, privacy and regulatory requirements. While many organizations deploy security differently, there are patterns and features that are commonly used by most organizations. Here are the most relevant controls to Define, Deploy and Monitor your security posture according to our best practices.

Define
Our Best Practice guides provide a detailed overview of the main security controls we recommend for typical and highly secure environments — based on what we see working in partnership with our most security-conscious customers.
Review these documents to get:
- A simple checklist for the key security controls that are most prevalent among our customers
- Threat models with the top security risks faced by our customers along with the specific controls to address them
- An appendix with descriptions, practitioner context and links for these key controls
Check out our security best practices for AWS, Azure and GCP
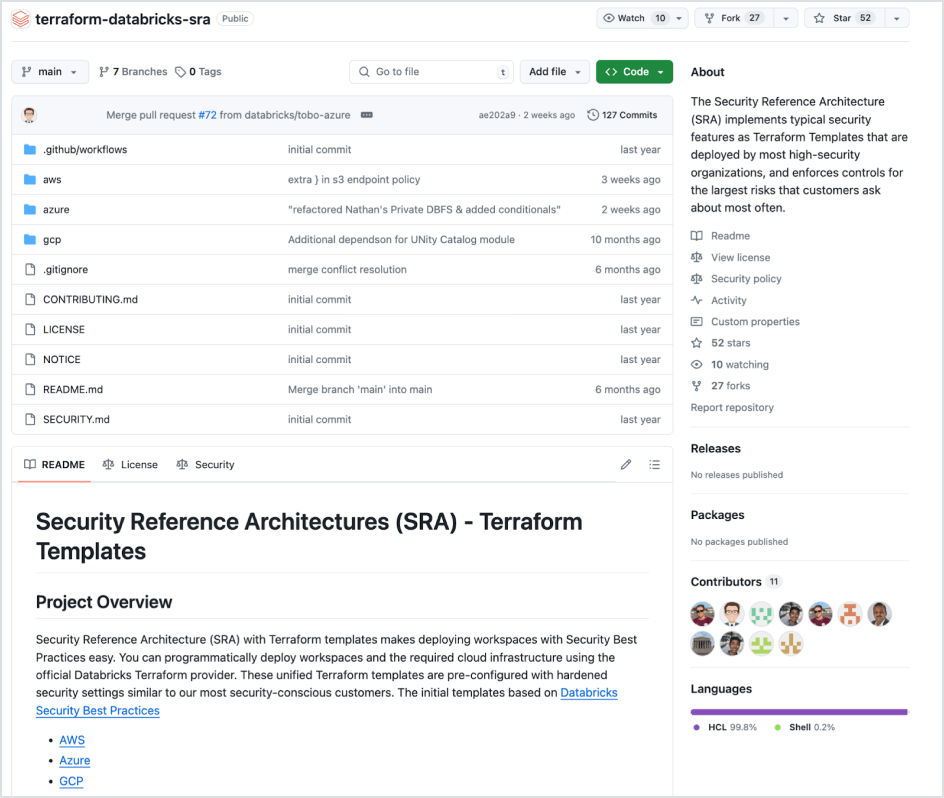
Deploy
Our Security Reference Architecture (SRA) Terraform templates make it easy to automatically create Databricks environments that follow these security best practices.
While securing a single workspace is straightforward with the checklist in our Best Practices guide, aligning an automation that has many workspaces can be very complex. Having terraform templates that include security from the start makes that much easier.
Check out our GitHub repo to get started on AWS, Azure and GCP
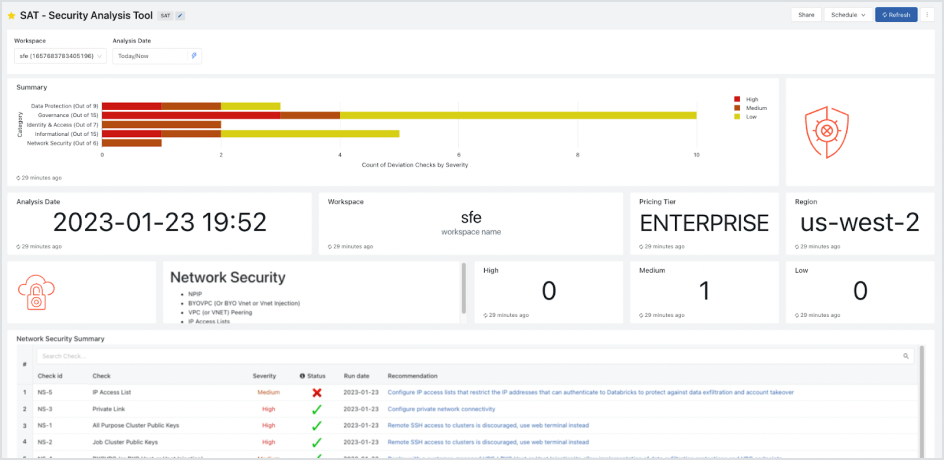
Monitor
Our Security Analysis Tool (SAT) continuously monitors the security posture of your Databricks Data Intelligence Platform in accordance with these security best practices.
With these resources, you can easily follow best practices when you deploy your workspace. But how do you make sure it stays that way? And if you’re an existing customer, how easily can you review all your workspaces to see how they compare with our best practices? The Security Analysis Tool is built for exactly these scenarios.
Check out our GitHub repo to get started on AWS, Azure and GCP
Additional resources
Learn more about securing your Databricks Data Intelligence Platform and mitigating the latest wave of AI security risks with the following resources:


